Smarter data management.
Stronger security.
CeTu recognized in the Gartner® Market Guide for Telemetry Pipelines & Gartner® Hype Cycle™ for Security Operations, 2025


Analyze, Enrich, Route: Manage Data With Purpose
With data volumes accelerating across cloud, AI workloads, SaaS, identity, and other attack surfaces, blind spots and noise are increasing exponentially — creating new hiding spots for adversaries.
Intelligently ingest log data at scale. Enrich data streams in real-time for immediate actionability. Accelerate detection & response. Dramatically lower SIEM costs & operational overhead.
 100%See 100% of Your security data
100%See 100% of Your security dataBolster defenses. Expose data gaps and waste.
Use AI-powered analysis of your SIEMs and logs to uncover blind spots & unnecessary data. Gain visibility to intelligently reduce costs. Contextually identify missing detections & logs (CloudTrail, VPC, etc.) to stop breaches faster. Alert on IOCs & anomalies – in real-time – before logs are even ingested by the SIEM.
 80%Cut SIEM ingest costs by up to 80%
80%Cut SIEM ingest costs by up to 80%Slash costs. Build for scale.
Strategically distribute ingestion across SIEMs, data lakes, and low-cost cloud storage. Build a scalable, federated data architecture with dynamic, policy-driven pipelines that automatically analyze, normalize, filter, enrich, and route data to its optimum destination.
 50%Cut data engineering time by 50%
50%Cut data engineering time by 50%Usable by everyday engineers. Agentless.
Unlike legacy pipeline tools that rely on engineers to manually locate and trim unnecessary data, our SecOps-aware AI and graphical no-code interface enable engineers – without scripting or data science expertise – to deliver ROI in days vs. months or years.
.png)
Analyze, Enrich, Route: Data With Purpose
CeTu transforms raw logs into meaningful signals and then routes data anywhere it’s needed – including SIEMs, data lakes & cloud storage – and always in the right format.
Data Analysis
Gain clarity before acting. CeTu analyzes your sources, SIEM, and detection logic to identify what’s in use, what’s redundant, and what’s missing, ensuring data decisions are driven by security and operational needs.
Data Enrichment
Build dynamic pipelines easily with our no-code interface, or use Zoe, our AI assistant, to create them in natural language. Filter noise, auto-normalize unstructured logs, and enrich logs with threat intel & context to transform raw data into meaningful signals.
Data Routing
Simplify telemetry management and deliver data to every destination instantly. CeTu acts as a flexible, policy-based hub for continuous change, routing to multiple targets simultaneously and automatically formatting data for each one.
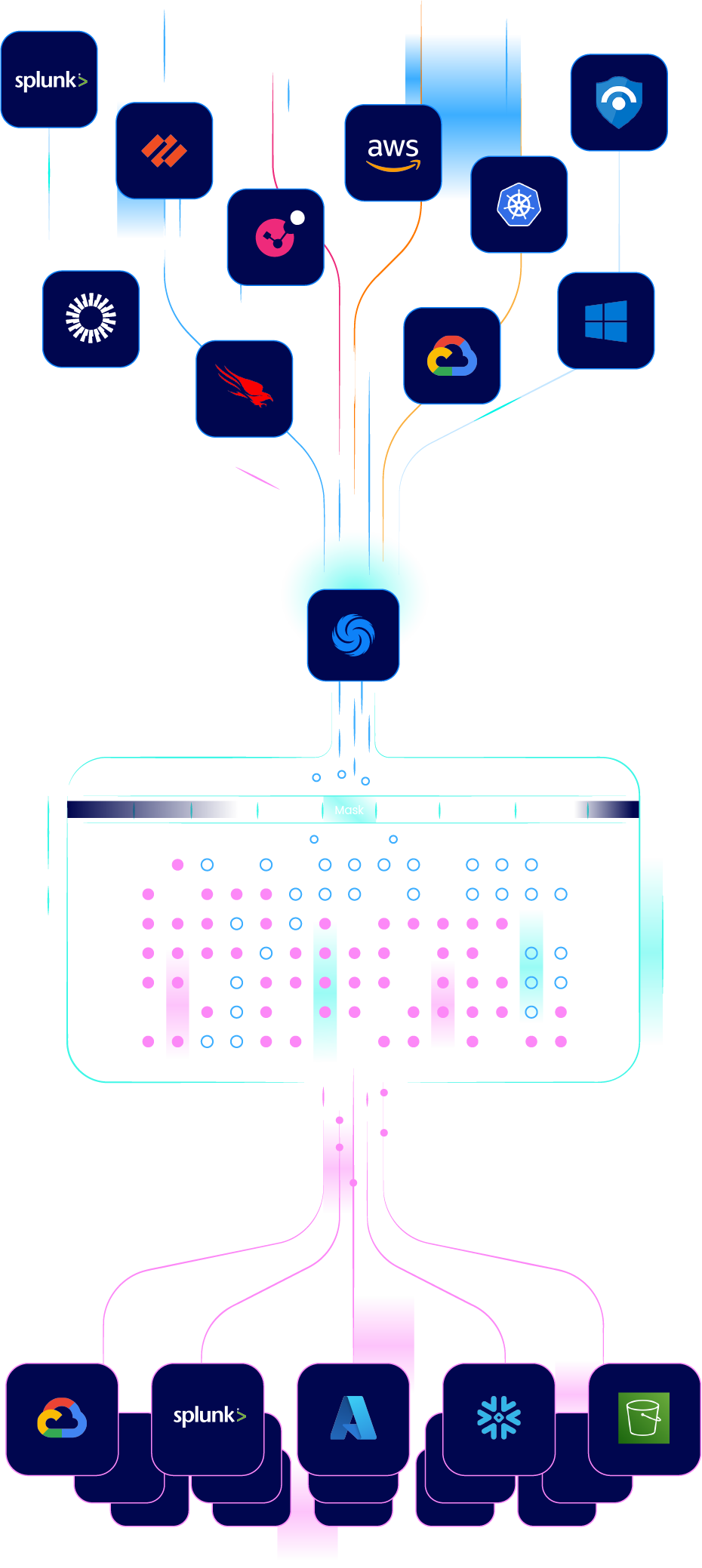
Built for Security Teams. Powered by AI
CeTu’s AI-powered platform removes the bottlenecks that slow security teams down - automating onboarding, cutting noise, and strengthening detections so you can act with clarity and confidence.
Connect Faster
Onboard sources in minutes with low-code/no-code pipelines, hundreds of built-in connectors, and AI-assisted parsing that eliminates manual regex. Just describe your goal in natural language, and CeTu builds the pipeline.
Route Smarter
AI-driven SIEM analysis highlights high-value data, filters out waste, enriches what matters, and routes seamlessly to multiple destinations, formatted automatically for each one.
Detect Reliably
AI-powered validation ensures telemetry is aligned with detection logic, enriched with context, and free of coverage gaps - so detections fire when they should.
.avif)
See Your SIEM in Action
Run CeTu’s InsightScan to instantly measure coverage, waste, and gaps in your environment.
Reduction
Data Sources
Assets
Detection Rules
Built by cybersecurity veterans.
The team behind CeTu has decades of experience designing scalable, intelligent systems for enterprise security teams.
Backed by TOP investors:


Mickey Boodaei
CEO, Transmit Security. Co-founder of Imperva and Trusteer. Early investor in Island, Preempt Security, Aorato.


Rakesh K. Loonkar
President & Co-Founder, Transmit Security. Early investor in Palo Alto, Zscaler, Armis., Salt Security, Abnormal.


Mike Fey
Co-Founder & CEO, Island. Former President/COO of Symantec & GM/CTO of McAfee.


Dan Amiga
Co-Founder & CTO, Island. Former Founder/CTO of Fireglass. Founding investor in Axis, Cycode, Cyclops, ScaleOps.


Udi Mokady
Founder & Executive Chairman, CyberArk (acquired by Palo Alto Networks).


Resources
Lower costs. Better security. C’est tout.
- 80%
Lower SIEM Ingest Costs
- 50%
Faster Data
Engineering - 0
Coding or Data
Science Skills
Required